Guides
Our Guides provide readers with comprehensive, step-by-step guides on how to enhance their digital privacy and online security. We cover topics such as secure web browsing, secure messaging, email encryption, and mobile phone security.
Our articles provide in-depth guidance on how to correctly utilize tools and software, as well as effective methods for creating strong passwords, managing online accounts and privacy settings, and recognizing potential cyber threats. We also identify potential vulnerabilities, and provide instructions on how to address them effectively.
Whether you are an individual user or a business owner, our Guides blog category provides the resources necessary to understand and implement effective strategies for online security and privacy. Stay informed and up-to-date on the latest techniques and tools for ensuring your online safety with our easy-to-follow guides.

Guides
Mobile Phone Security: Why It Matters and How to Protect It
In the digital age, smartphones are a vital part of our daily lives. They store our personal information, facilitate communications, ...

Guides Services Tools
Secure Messaging Apps: A Comparison of Popular Encrypted Messaging Platforms
In today’s digital age, privacy and data security have become increasingly important. As a result, many people are turning to ...
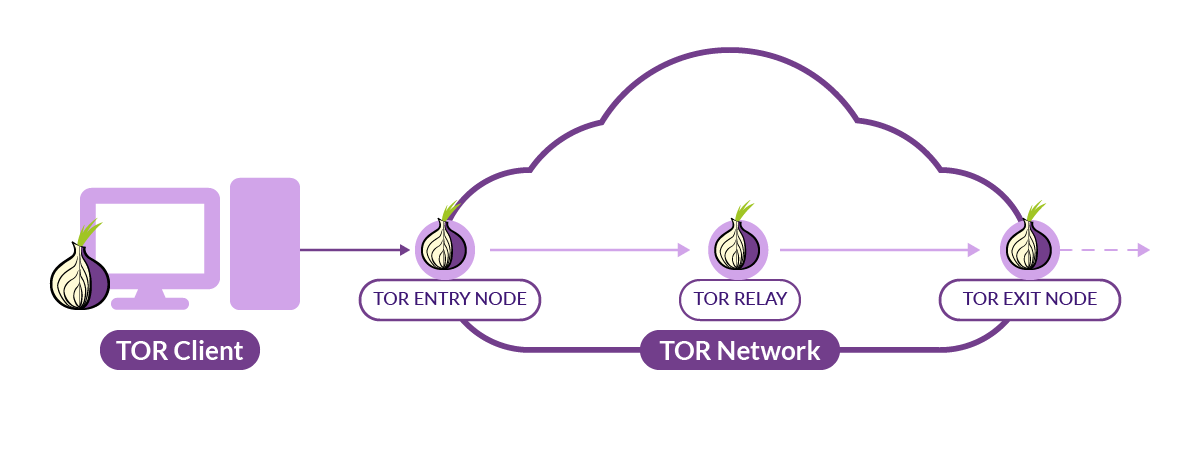
Anonymity Guides Privacy
Basic overview of Tor: Using Tor vs VPNs
The internet is an amazing tool but it comes with risks. Your online activities can be monitored, tracked, and used ...

Guides
Common Types of Cyber Attacks and How to Prevent Them
Cyber attacks are a constant threat to individuals and businesses alike. They can lead to data loss, financial loss, and ...

Guides
Best Practices for Email Security
Email is one of the most commonly used communication channels, but it also presents significant security risks due to the ...

Guides
Best Practices for Securing Internet of Things (IoT) Devices
The Internet of Things (IoT) refers to the connection of everyday devices to the internet, from smart thermostats to industrial ...

Guides
The Importance of Backing Up Your Data and How to Do It
Losing important personal files or sensitive business data can be devastating. However, backing up your data regularly can help prevent ...

Guides
Tips for Protecting Your Online Identity in a Digital World
Protecting your online identity is crucial in today’s digital world, where personal information can easily be stolen or compromised. Here ...

Guides
Understanding Data Encryption and Its Importance for Digital Privacy
Data encryption is a security measure used to protect sensitive data from unauthorized access. It can be used in various ...

Guides
Tips for Spotting and Avoiding Phishing Scams
Phishing scams are a common form of cyber attack where scammers try to obtain sensitive personal or financial information through ...